Network Detection & Response
Network detection and response (NDR) is a field of cybersecurity that detects malicious activity through the analysis of network traffic. Like endpoint detection and response (EDR), NDR solutions do not prevent malicious activity. Instead, detection and response solutions aim to stop attack activity in progress before it can result in harm. NDR is distinct from EDR in that it does not use an agent to gain insight into malicious activity, relying instead on a network or virtual tap for analysis of traffic across on-premises and cloud workloads.

According to Gartner and IDC
NDR was the second-fasting growing segment of the security market in 2020, growing at a 25 percent compound annual growth rate (CAGR).
NDR solutions analyse network traffic to detect malicious activity inside the perimeter—otherwise known as the east-west corridor––and support intelligent threat detection, investigation, and response.
Using an out-of-band network mirror port or a virtual tap, NDR solutions passively capture network communications and apply advanced techniques, including behavioural analytics and machine learning, to identify both known and unknown attack patterns. This data can also be used to perform real-time investigation into post-compromise activity and to forensically investigate incidents. While not all NDR solutions decrypt network traffic, the most advanced solutions provide secure decryption capability to help identify threats hiding within encrypted traffic.
![]()
DIFFICULT TO EVADE
So threats can’t hide
![]()
COVERT & AGENTLESS
Stay stealth
![]()
GROUND TRUTH
From core to edge to cloud
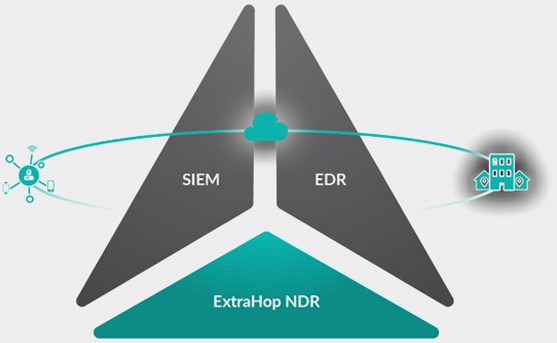
But what does this mean in practice? The business and IT benefits include:
- Reduce exposure to risk and the financial and reputational damage associated with serious data breaches and ransomware-related
outages - Empower under-pressure SOC teams with optimized threat detection and response
- Enhance IT efficiency with a single workflow for threat detection,
response and forensics - Close compliance gaps
- Save money with a single, powerful detection and response tool that works across on-premises, cloud, and hybrid environments
- Monitor threats to IoT devices which don’t have endpoint security
installed - Support digital transformation projects with the confidence that they will be built on secure foundations




















